Cybercriminals Behind Salesforce Voice Phishing Launch Ransom Website Threatening Fortune 500 Data
Group behind voice-phishing that stole Salesforce records launched a site threatening to publish stolen data from Fortune 500 firms unless ransoms are paid.
Page views: 2
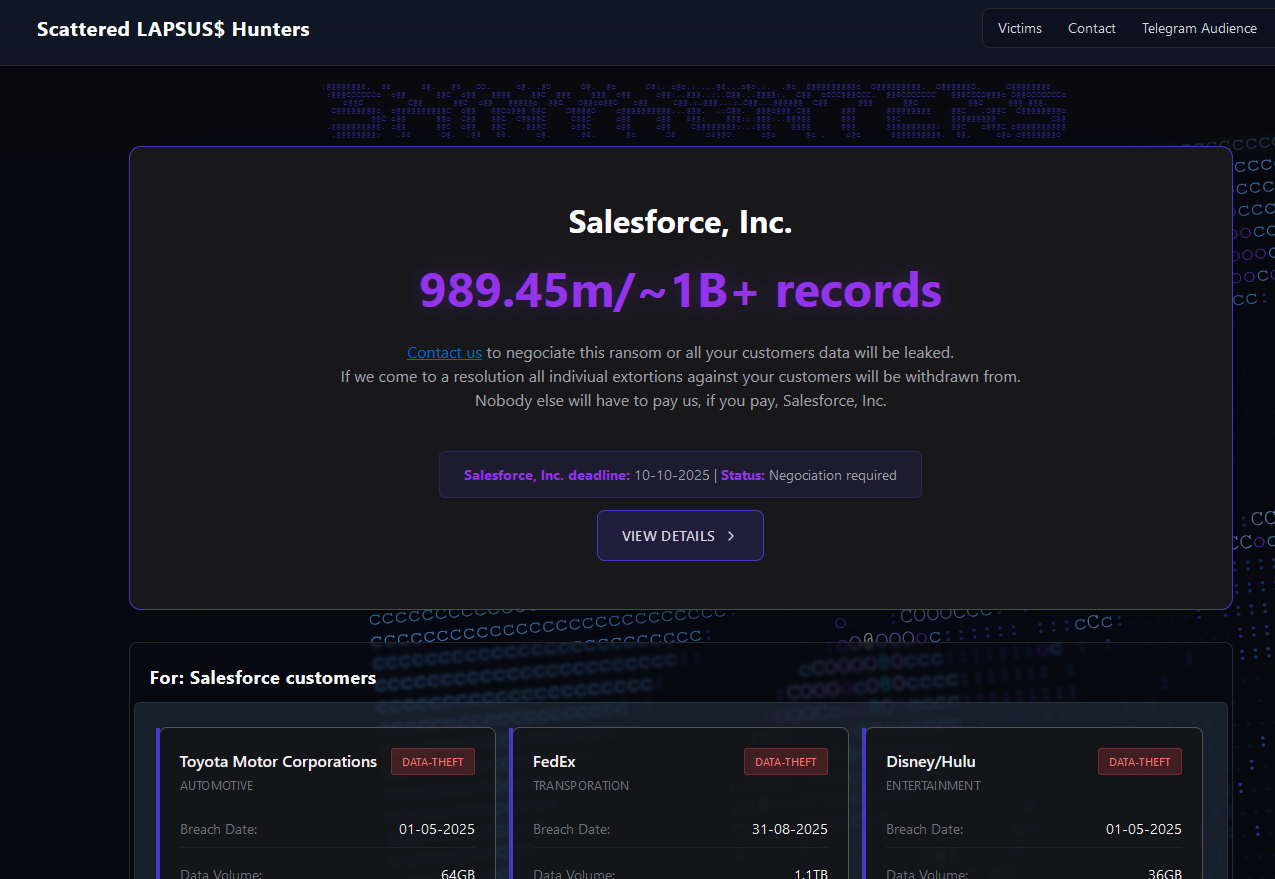
A cybercriminal group that used voice phishing attacks to siphon more than a billion records from Salesforce customers earlier this year has escalated its campaign. The group launched a public website threatening to publish stolen data from dozens of Fortune 500 firms if ransoms are not paid, signaling a new phase in high-profile data extortion.
Security researchers say the operation began with sophisticated voice phishing — or vishing — that duped employees and contractors into divulging access credentials. Once inside, attackers harvested customer records and sensitive files. The group’s claim of responsibility for a recent Discord user data breach and for stealing terabytes of sensitive files from thousands of Red Hat customers has heightened concerns across the cybersecurity community.
The website serves multiple purposes: it publicly pressures victims, advertises the group’s reach, and lists alleged victims to increase leverage for ransom demands. Threat actors often use such leak sites to create urgency and reputational risk, forcing companies to weigh data exposure against paying attackers. For Fortune 500 firms, the stakes include regulatory fines, customer churn, and long-term damage to brand trust.
This string of breaches underscores several persistent vulnerabilities: weak authentication, inadequate employee training against social engineering, and insufficient monitoring of third-party access. Voice phishing is effective because it targets human trust rather than software defenses, making multi-layered security essential. Companies should enforce strong multi-factor authentication (MFA), conduct regular vishing simulations, and tighten privileges for third-party integrations with platforms like Salesforce and Red Hat.
Incident response plans must be ready to handle ransom threats and public leak sites. Organizations should immediately assess exposed systems, revoke compromised credentials, and notify affected customers and regulators as required. Engaging digital forensics and legal counsel helps determine the scope and response options while reducing the risk of further leakage.
As this situation develops, corporate security leaders should prioritize patching, continuous monitoring, and vendor risk assessments to reduce attack surface. For individuals, be wary of unexpected calls requesting login details and report suspicious activity to your IT team. Monitoring updates from trusted cybersecurity sources will help organizations and users stay informed as investigators track the group’s next moves.
Published on: October 8, 2025, 8:02 am



